overleaf template galleryLaTeX templates and examples — Recent
Discover LaTeX templates and examples to help with everything from writing a journal article to using a specific LaTeX package.

A project report template for use at the Indian Institute of Technology Gandhinagar, India

This template contains instructions for authors planning to submit a paper to the Journal of Plasma Physics. You can use it in Overleaf to write and collaborate online in LaTeX. Once your article is complete, you can submit directly to JPP using the ‘Submit to journal’ option in the Overleaf editor. For more information on how to write in LaTeX using Overleaf, see this video tutorial, or contact the the journal for more information on submissions.

This is a LaTex template for assignments, basically for math problems. Information and school logos can be easily customized. Hope you enjoy this one. Should you have any questions, please contact me via yzhaodx@connect.ust.hk.

Custom resume template in LaTeX with automatic fit to page function. Built and compiled in LuaLaTeX.

This is the official (OMEA-approved) year-2022 version the thesis template designed for the students of the Department of Physics at the National and Kapodistrian University in Athens, Greece.

This is a report template for bachelor, master, and PhD students at the Faculty of Sciences of Sfax
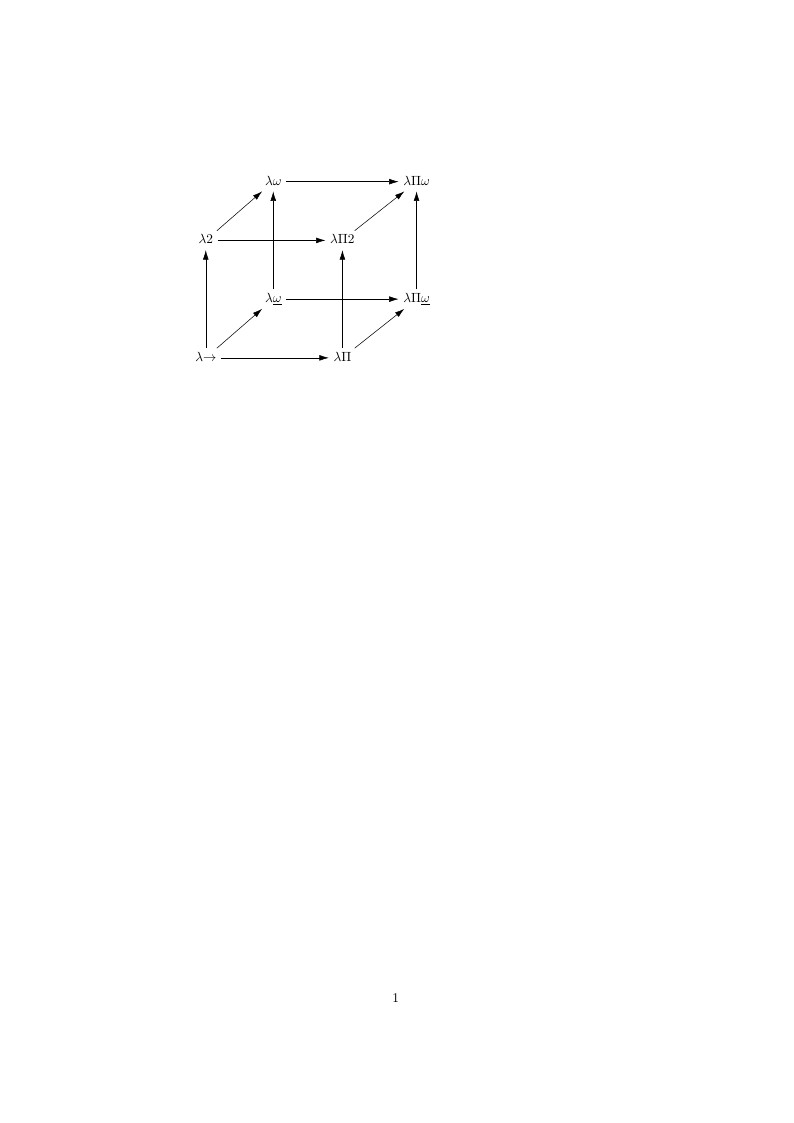
Computer Science. Type theory. Famous Lambda Cube invented by Henk Barendregt.

Classe anglaise pour la rédaction des mémoires, rapports et thèses conformes aux normes de présentation de l'UQAM-Département de mathématiques.

Report template for Praxisprojects @ colaps, UDE
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.